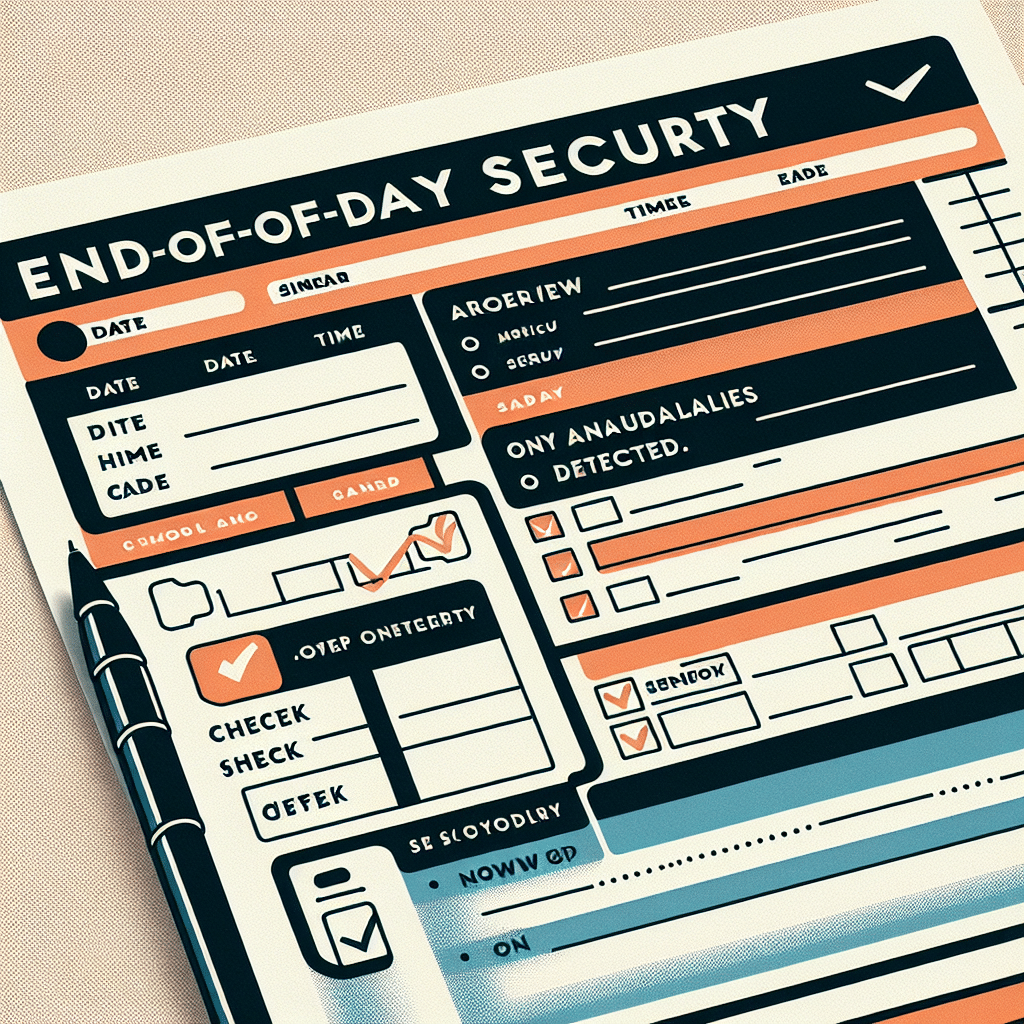
To effectively record end-of-day security checks, organizations typically utilize a structured form known as the “End-of-Day Security Checklist.” This form is designed to ensure comprehensive documentation of all security protocols adhered to at the close of business. Commonly, it includes sections for logging the completion of security rounds, checking the status of surveillance systems, verifying the locking of entry points, and noting any irregularities or incidents. By utilizing a standard form, businesses can maintain consistency in security practices, enhance accountability among staff, and facilitate adherence to regulatory requirements. This detailed record can serve as both a reference and an audit trail to ensure continuous improvement in security measures.
Understanding the Importance of End-of-Day Security Checks
As a security professional or business owner, ensuring the safety and integrity of your premises requires diligent efforts, especially at the end of the day. End-of-day security checks are a critical component of an effective security management strategy. They help mitigate risks associated with theft, vandalism, and unauthorized access. A well-documented process provides accountability and improves security measures over time.
What Is an End-of-Day Security Check?
An end-of-day security check refers to a systematic assessment conducted at the close of business hours to ensure that all security protocols are followed. This process typically includes verifying the status of alarms, locks, surveillance cameras, and overall premises security. By implementing these checks, organizations can identify vulnerabilities and reduce the likelihood of security breaches.
What Form Is Used to Record End-of-Day Security Checks?
The preferred form for recording end-of-day security checks is often referred to as the “End-of-Day Security Checklist” or “Security Patrol Log.” This document may vary based on the organization’s size and nature of operations but commonly includes the following elements:
- Identification Information: Name of the security personnel, date, and time of the check.
- Checklist Items: Specific tasks to be completed, such as ensuring all doors are locked, checking alarm systems, and verifying that surveillance equipment is operational.
- Incident Reporting: A section for detailing any anomalies, incidents, or suspicious activities observed during the security check.
- Signature Line: To confirm that the security personnel conducted the checks and acknowledged any findings.
Examples of End-of-Day Security Check Forms
Many businesses have adopted customized checklists tailored to their specific security needs. Some examples include:
- Retail Security Checklists: Commonly used in retail environments to ensure that merchandise is secure before closing.
- Corporate Office Security Forms: Focused on interior checks, access control, and alarm systems in office buildings.
- Industrial Facility Checklists: Address safety gear, machinery locks, and hazardous materials management.
Best Practices for Implementing End-of-Day Security Checks
Implementing effective end-of-day security checks involves several best practices:
- Standardization: Utilize a standardized form to ensure consistency across shifts and personnel.
- Training: Provide regular training to security staff on how to complete the checklist and respond to incidents.
- Regular Reviews: Continuously review and revise the checklist to adapt to changing security needs and enhance the process.
- Documentation: Maintain a secure archive of completed checklists for references in audits and evaluations.
Addressing Concerns and Counterarguments
While some may argue that end-of-day checks can be redundant, it’s crucial to realize their value in enhancing overall security. Organizations risk neglecting critical security protocols when checks are not documented. Critics also raise points about human error in the manual completion of forms. Utilizing digital platforms or mobile applications can mitigate this risk, ensuring that entries are time-stamped and verified through image documentation where necessary.
Conclusion
End-of-day security checks are a fundamental part of a robust security strategy. The appropriate form—typically an End-of-Day Security Checklist, plays a vital role in documenting findings and ensuring accountability. By adhering to best practices and continually refining the security checklist, organizations can foster a culture of safety and readiness, minimizing risks while improving security measures across the board.
FAQs
What should I include in an end-of-day security check form?
Include identification information, checklist items (such as verifying locked doors and operational alarms), a section for incident reporting, and a signature line for personnel confirmation.
How often should I review the end-of-day security checklist?
The checklist should be reviewed and updated regularly—ideally on a quarterly basis or whenever there are significant changes in security protocols.
What happens if an incident is reported during the checks?
Any incidents reported should be documented in detail in the form, and a follow-up protocol should be initiated according to the organization’s incident response plan.
Can I customize the security check form for my business?
Absolutely! It’s important to tailor the checklist to meet your specific security needs while ensuring that fundamental security assessments are maintained.
Is there software available for recording end-of-day checks?
Yes, there are various security management software solutions available that can help streamline the recording of end-of-day checks, allowing for more efficient data management and reporting.